Connecting OpenIdM with Microsoft Active Directory – How to set it up!
Posted 11 years ago by lfolta
This article is about setting up ForgeRock’s Open Identity Management with Microsoft Active Directory using standalone .NET Connector Server.
About OpenIDM & OpenICF
OpenIDM communicates with various kinds of resources from simple files (XML, CSV) to more complex ones, like various LDAP implementations and SQL databases. This communication is provided via Open Identity Connector Framework and Toolkit (OpenICF). If, for some reason, access libraries cannot be build-in to OpenIDM (cannot be included inside Java Virtual Machine) an external connector server is needed. This article covers deployment of OpenIDM on one machine and external .NET Connector Server where remote connector is implemented on second remote machine. In this deployment .Net Connector Server provides a way to connect OpenIDM with Microsoft Active Directory as depicted in below diagram: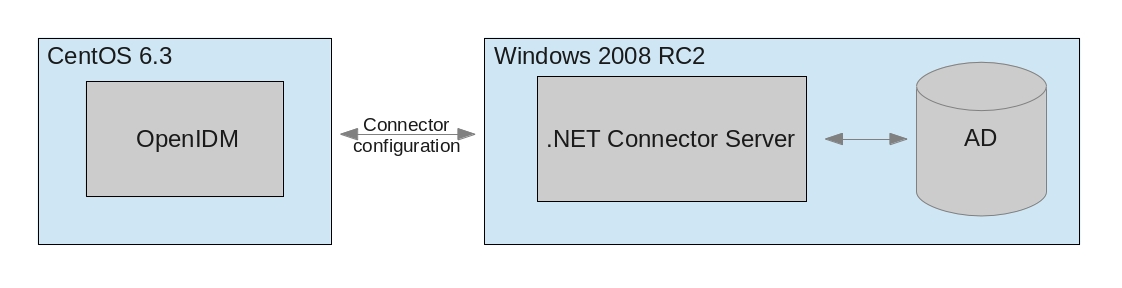
Prerequisites
- Windows 2003 or 2008
- .NET Framework 4.0
- Microsoft Active Directory – In this setup I used the AD bundled with Windows 2008 RC2 SP1
- OpenIDM 2.1.0. revision 1395
Installing .NET Connector Server on Windows
- Download connector server from here (tested on build #23 )
- Execute the downloaded .msi file. Just follow the wizard. It will walk you through the whole process step by step. Upon completion, the Connector Server will be installed as a windows service called “Connector Server”.
Starting and Stopping the Connector Server
- You can start or stop the server using Microsoft Services Console. Start -> type Services -> Services
- Also you can start the server from command prompt. Start -> type cmd -> cmd. Change the directory to where the Connector Server has been installed, by defaultProgram FilesIdentity ConnectorsConnector Server
C:> cd “Program Files (x86)Identity ConnectorsConnector Server”
and run the following command:
./ConnetorServer.exe /run
Configuring the .NET Connector Server
- Start the Microsoft Services Console (Start -> type Services -> Services ). Check to see if the Connector Server is currently running. If so, stop it. From a command prompt (Start -> type cmd), set the key for the connector Server. This is done by changing to the directory where the connector server was installed and executing the following command:
./ConnectorServer.exe /setkey <newkey>
where
<newkey>
is the string value. This key is required by any client that connects to this Connector Server.
- See the ConnectorServer.exe.config for addtional configuration. The port, address, and SSL settings are in the tag called AppSettings, and look like this:
<add key="connectorserver.port" value="8759" /> <add key="connectorserver.usessl" value="false" /> <add key="connectorserver.certificatestorename" value="ConnectorServerSSLCertificate" /> <add key="connectorserver.ifaddress" value="0.0.0.0" />- connectorserver.port – Sets the port
- connectorserver.ifaddress – Accepting connections from particular address or all (0.0.0.0)
- connectorserver.usessl – Turns on/off the SSL
- connectorserver.certifacatestorename – If using certificates, put there your certificate store name
Any configuration changes will require the connector server to be stopped and restarted.
- Now, you need to add the active directory connector. Do it so by downloading active directory connector (tested on build #15) and simply unzipping it to Connector Server folder.
- Start the Connector Server service (from Microsoft Service Console).
- Make sure you have your firewall either turned off or add rule to your firewall to open port which you have set in ConnectorServer.exe.config
Configuring OpenIDM
- When you configure remote connectors, you must use the connector info provider service to connect through remote connector servers. The configuration is stored in the configuration file, openidm/conf/provisioner.openicf.connectorinfoprovider.json. A sample can be found in openidm/samples/provisioners/.
- Make sure the openidm is running and copy the provisioner.openicf.connectorinfoprovider.json to /path/to/openidm/conf and edit it according to your needs. In my case the file is provisioner.openicf.connectioninfoprovider.json
$ cd path/to/openidm $ cp samples/provisioners/provisioner.openicf.connectorinfoprovider.json conf/
- As next step you need to create connector file provisioner.openicf-ad.json in conf/ directory. The file should look like the following one provisioner.openicf-ad.json
- Edit the configurationProperties according to your Active Directory setup and also make sure that the bundleVersion is the SAME version as ActioveDirectory.Connector.dll in Windows Connector Server folder. (Right click on the dll -> properties -> tab details -> Product version)
- Check if the connector was installed properly. In openIDM console run following command:
scr list
among the all installed modules you should see (number can differ):
[ 24] [active ] org.forgerock.openidm.provisioner.openicf
see the content of this connector by:scr info 24
(use the number from your list)
and you should see the content of connector.
- Now, you need to create sync.json where you define mappings of various attributes and behavior during reconciliation. A simple sync.json could look like this: sync.json
After configuring sync.json and placing it to conf/ directory the system should be ready.
Testing the setup
- Verify installed connectors (following command has to be on one line):
curl --header "X-OpenIDM-Username: openidm-admin" --header "X-OpenIDM-Password: openidm-admin" --request POST "http://localhost:8080/openidm/ system?_action=CREATECONFIGURATION" | python -mjson.toolthis command lists all installed connectors. In the list you should see an Active Directory connector.
…
{
“bundleName”: “ActiveDirectory.Connector”,
“bundleVersion”: “1.0.0.0”,
“connectorHostRef”: “dotnet”,
“connectorName”: “Org.IdentityConnectors.ActiveDirectory.ActiveDirectoryConnector”,
“displayName”: “Windows Active Directory Connector”
}
…
- Running reconciliation (following command has to be on one line):
$ curl --header "X-OpenIDM-Username: openidm-admin" --header "X-OpenIDM-Password: openidm-admin" --request POST "http://localhost:8080/openidm/recon?_action=recon& mapping=systemADAccounts_managedUser"and as result you should get reconciliation id.
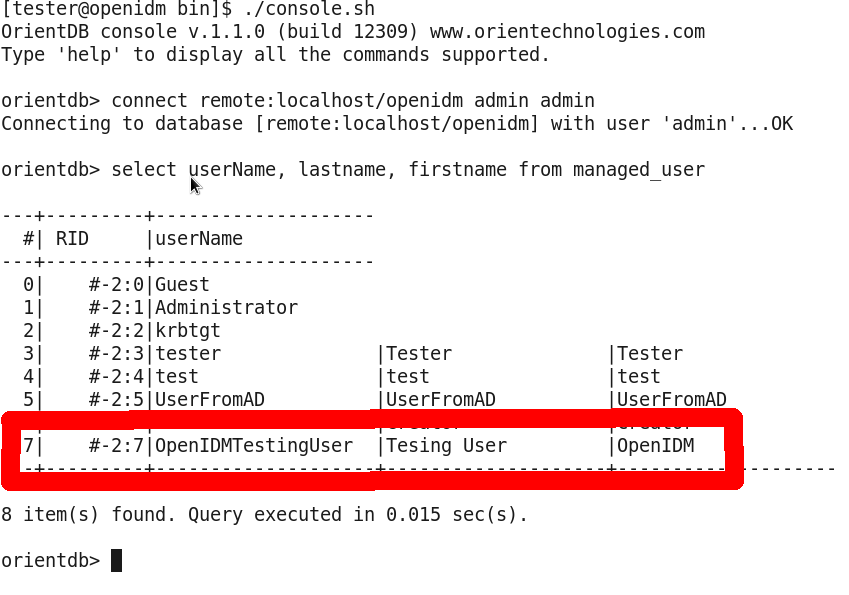
{“_id”:”0629d920-e29f-4650-889f-4423632481ad”} - Check in OpenIDM internal repository (OrientDB or MySQL) if the users were reconciled. How to connect to repo is described here (OrientDB) or here (MySQL).
Here is an example of output from OrientDB after reconciling. The red marked user has been reconciled from Active Directory.